Why Your Business Needs IT Support Services
Staying out of the digital landscape is no longer an option for a successful business. Any issues with IT can have huge impacts on your business. This has made businesses strongly reliant on high-quality IT support services. Some of the services that you will need are troubleshooting issues, network maintenance, and technical assistance.
Having the right IT support, whether you are a small startup or large multinational business, can be the difference between operational efficiency and costly downtime.
Why is Managed IT Support Better?
Managed IT support means utilising a third-party service provider for your company’s IT management and operations. Though you may be reluctant to entrust it to an outsider, it is actually a much better option.
By having a company that specialises in IT support to help your business lets your technology run efficiently without the burden of recruiting and maintaining an in-house team. It can greatly help cut down on costs. Also they will stay updated on the latest updates and trends so you don’t have to and lets you focus more on your core business.
Moreover, most of these IT support services offer a help desk that resolves any issues promptly. Getting access to advanced technological solutions lets your business stay efficient and competitive in a rapidly growing digital landscape.
What services can you expect?
- Network Management: Ensuring your network is secure, stable, and optimised is crucial. This allows your company to operate efficiently and can cut down on unwanted delays.
- Data Backup and Recovery: Loss of important data can really push back your business resulting in huge financial losses. So protecting your data with reliable backup solutions can be what makes or breaks your business.

- Software Updates and Maintenance: With new technology and updates coming out frequently it is important to keep systems updated. Having updated solutions means improved efficiency and security.
- IT Help Desk: Professional assistance to resolve any technical issue promptly is crucial, especially if your business caters to a wide range of customers.
IT support for small and large businesses
Regardless of the size of your company, business IT support is an indispensable part of success. Small business IT helps you cut down hefty costs of investment in IT infrastructure by providing cost-effective solutions and helping to scale operations. Larger businesses would require tailored IT strategies that can meet their growing and complex needs.
Pros of having external IT service and support

- Increased Productivity: With professional IT support your team will not be hindered by technical issues and can focus well on their tasks. Additionally, you can allocate more resources to the actual running of your business.
- Cost Savings: Downtime can be a cause of major revenue loss so it is important to have a team that can provide proactive maintenance and quick solutions.
- Reliable Security: Cyber threats are a growing issue that can result in the loss or leak of confidential data of both the company and its clients. So, it is imperative that you have IT support teams that implement robust security measures to protect your business from such threats.
- Access to Expertise: Having a team of experts who are updated on the latest trends and advancements will be a huge boost for your business. They can keep track of updates and make upgrades as needed.
Professional IT support is a necessity for any business to thrive in a competitive environment. For businesses in Canberra and Griffith, partnering with a reputable IT support services provider can unlock new levels of efficiency, security, and growth. Make the smart choice today and transform your business with Nxt IT. Schedule your personalised IT support assessment today!
Top ways to strengthen protection for IoT devices in OT

To ensure IoT devices that support OT aren’t compromised from cyber attacks, IT teams can implement zero-trust security, digital twins and supply chain measures.
Over the past few decades, we’ve seen cyberthreats evolve from tools to smart weapons, extending their reach as botnets that develop into advanced persistent threats and kill chains.
As IoT matures, the focus in cyberwarfare has turned to protecting devices. Traditional IT and operational technology (OT) are converging, and cybersecurity professionals must explore better ways to protect both domains.
An evolving threat landscape
The threat landscape has changed dramatically, and attacks are increasingly sophisticated. Bad actors may launch coordinated attacks that attack key infrastructure. Nation-state attackers launch ransomware attacks that use weaponized cryptography. Malware propagates from threat actors to sensors, controllers and actuators.
As attacks become more complex, industrial environments are increasingly vulnerable. Most brownfield and greenfield devices in these deployments lack cyber resilience by design, which leaves organizations unprepared.
What distinguishes threats in 2022 from earlier attacks? Fundamentally, the difference is that today’s hackers have a better understanding of how to sidestep detection and prevention controls. Traditional IT security was built with a focus on examining network traffic and utilizing rules-based firewalls, threat intelligence, and policy-based intrusion and anomaly detection.
It is challenging to adapt these IT security strategies for OT, as devices and humans have dramatically different vulnerabilities. Unlike the predictable behavior of devices, human psychology is tougher to proactively address.
Aligning security to industry trends
Device protection requires an approach based on a horizontal platform of transitive trust, together with a vertical pillar of integrated trust. For an effective strategy, organizations must align security to several industry trends.
1 Digital transformation
Digital transformation for IoT devices applies AI and machine learning (ML) to enhance operational efficiency and digital privacy, as well as enable data sharing. AI requires intelligence in both the network and devices to support continuity and runtime integrity of services in automation-powered industrial applications.
ML offers operational efficiencies, as it builds observations for evidence-based abductive reasoning models, condition-based maintenance for longer service life, and telemetry for quality improvements and design innovations.
2 Zero-trust security
A zero-trust model for security applies a volume, velocity and variety challenge for real-time, low-latency line-of-business applications. Volume refers to devices, cryptographic keys, and certificates for device identification and authentication. Velocity refers to automation to support protective measures for transfer of ownership, as well as key and certificate lifecycle management. Zero-trust models also support a variety of global cryptographic algorithms, utilizing an abstraction layer and restricted key usage.
3 Supply chain trust
Building trust in the supply chain is the third key trend. The supply chain attack surface is highly elastic, with many visibility gaps. Blind spots can range from silicon fabrication facilities to OEMs, device owners and operators, and connected devices.
Protection requires a horizontal trust chain beginning at the root of trust, with manufacturer- and device owner-issued identifiers, as well as cryptographic key usage based on the principle of least privilege. Supply chain security also requires a configurable software offering and certificate authority (CA). These offerings should not require cloud platform or CA lock-in to facilitate easy migration and optimize cost management.
4 Digital twins
AI initiatives also support digital twins for quality improvements and design innovation that build on telemetry and state synchronization. Organizations must plug security gaps between virtual and physical systems. They should also take steps to prevent compromises of the virtual digital twin by hackers that could enable them to expose the actual physical system.
Organizations should also enable event-based synchronization, with regular transfer of accurate and tamper-resistant data with low latency. IT teams synchronize the configuration state for trustworthiness with platform attestation and coordinate software updates with supply chain provenance.
5 Application security by design
Line-of-business applications should integrate security measures from the get-go. Their design should meet compliance requirements and risk management objectives, from resource-constrained sensors and actuators to controllers and edge gateways that extend into cyberspace.
As part of this security by design, applications should include protective controls for data protection and privacy, device authentication, remote recovery and integrity monitoring.
An ecosystem approach
In OT environments, the risk model is based on compliance, security and safety considerations. Unlike threats, every risk has a measurable cost and benefit. For example, a compromised factory key compromise might result in a device recall or truck roll to remediate the issue.
Hackers are familiar with most detection and prevention tools and methods. Given the volume of events with low signal-to-noise ratio and the cost of post-breach forensics to generate threat intelligence, traditional cybersecurity strategies are simply not sustainable.
As IoT use cases mature, IT and OT ecosystems require close alignment. OT security brings together network operations centers, security operations centers (SOCs), device management systems (DMSes) and application management systems. Organizations should seek to give SOC operators supply chain tamper resistance, device intelligence and indicators of risk for remote maintenance and recovery of OT devices.
For DMS operators, capabilities such as authenticated device identifiers for secure onboarding, on-device protection of cryptographic artifacts, secure boot sequence and integrity monitoring options offer comprehensive protection.
The IoT ecosystem, workflows and technologies at its foundation require a collaborative mindset that extends from the silicon vendor to manufacturers, operators and service providers to prevent and diffuse cyber attacks.
SOURCE: https://www.techtarget.com/iotagenda/post/Top-ways-to-strengthen-protection-for-IoT-devices-in-OT
The Worst Hacks and Breaches of 2022 So Far
From cryptocurrency thefts to intrusions into telecom giants, state-backed attackers have had a field day in the year’s first half.

WHETHER THE FIRST six months of 2022 have felt interminable or fleeting—or both—massive hacks, data breaches, digital scams, and ransomware attacks continued apace throughout the first half of this complicated year. With the Covid-19 pandemic, economic instability, geopolitical unrest, and bitter human rights disputes grinding on around the world, cybersecurity vulnerabilities and digital attacks have proved to be thoroughly enmeshed in all aspects of life.
With another six months left in the year, though, there’s more still to come. Here are the biggest digital security debacles that have played out so far.
Russia/Ukraine Hacking
For years, Russia has aggressively and recklessly mounted digital attacks against Ukraine, causing blackouts, attempting to skew elections, stealing data, and releasing destructive malware to rampage across the country—and the world. After invading Ukraine in February, though, the digital dynamic between the two countries has changed as Russia struggles to support a massive and costly kinetic war and Ukraine mounts resistance on every front it can think of. This has meant that while Russia has continued to pummel Ukrainian institutions and infrastructure with cyberattacks, Ukraine has also been hacking back with surprising success. Ukraine formed a volunteer “IT Army” at the beginning of the war, which has focused on mounting DDoS attacks and disruptive hacks against Russian institutions and services to cause as much chaos as possible. Hacktivists from around the world have also turned their attention—and digital firepower—toward the conflict. And as Ukraine launches other types of hacks against Russia, including attacks utilizing custom malware, Russia has suffered data breaches and service disruptions at an unprecedented scale.
Lapsus$ Group’s Extortion Spree
The digital extortion gang Lapsus$ went on an extreme hacking bender in the first months of 2022. The group emerged in December and began stealing source code and other valuable data from increasingly prominent and sensitive companies—including Nvidia, Samsung, and Ubisoft—before leaking it in apparent extortion attempts. The spree reached its zenith in March when the group announced that it had breached and leaked portions of Microsoft Bing and Cortana source code and compromised a contractor with access to the internal systems of the ubiquitous authentication service Okta. The attackers, who appeared to be based in the United Kingdom and South America, largely relied on phishing attacks to gain access to targets’ systems. At the end of March, British police arrested seven people believed to have associations with the group and charged two at the beginning of April. Lapsus$ seemed to briefly continue to operate following the arrests but then became dormant.
Conti Cripples Costa Rica
In one of the most disruptive ransomware attacks to date, Russia-linked cybercrime gang Conti brought Costa Rica to a screeching halt in April—and the disruptions would last for months. The group’s attack on the country’s Ministry of Finance paralyzed Costa Rica’s import/export businesses, causing losses of tens of millions of dollars a day. So serious was the attack that Costa Rica’s president declared a “national emergency”—the first country to do so because of a ransomware attack—and one security expert described Conti’s campaign as “unprecedented.” A second attack in late May, this one on the Costa Rican Social Security Fund, was attributed to the Conti-linked HIVE ransomware and caused widespread disruptions to the country’s health care system. While Conti’s attack on Costa Rica is historic, some believe that it was meant as a diversion while the gang attempts to rebrand to evade sanctions against Russia over its war with Ukraine.
Decentralized Finance Platform Hacks
As the cryptocurrency ecosystem has evolved, tools and utilities for storing, converting, and otherwise managing it have developed at breakneck speed. Such rapid expansion has come with its share of oversights and missteps, though. And cybercriminals have been eager to capitalize on these mistakes, frequently stealing vast troves of cryptocurrency worth tens or hundreds of millions of dollars. At the end of March, for example, North Korea’s Lazarus Group memorably stole what at the time was $540 million worth of Ethereum and USDC stablecoin from the popular Ronin blockchain “bridge.” Meanwhile, in February, attackers exploited a flaw in the Wormhole bridge to grab what was then about $321 million worth of Wormhole’s Ethereum variant. And in April, attackers targeted the stablecoin protocol Beanstalk, granting themselves a “flash loan” to steal about $182 million worth of cryptocurrency at the time.
Data Theft From Health Care Providers
Health care providers and hospitals have long been a favorite target of ransomware actors, who look to create maximum urgency to entice victims to pay up in the hopes of restoring their digital systems. But health care data breaches have also continued in 2022 as criminals pool data they can monetize through identity theft and other types of financial fraud. In June, the Massachusetts-based service provider Shields Health Care Group disclosed that it suffered a data breach throughout much of March impacting roughly 2 million people in the United States. The stolen data included names, Social Security numbers, birth dates, addresses, and billing information, as well as medical information like diagnoses and medical record indicators. In Texas, patients of Baptist Health System and Resolute Health Hospital announced a similar breach in June that exposed similar data, including Social Security numbers and sensitive patient medical information. Both Kaiser Permanente and Yuma Regional Medical Center in Arizona also disclosed data breaches in June.
Chinese Hackers Breach Telecoms and More
At the beginning of June, the US Cybersecurity and Infrastructure Security Agency warned that Chinese government-backed hackers had breached a number of sensitive victims worldwide, including “major telecommunications companies.” They did so, according to CISA, by targeting known router vulnerabilities and bugs in other network equipment, including those made by Cisco and Fortinet among other vendors. The warning did not identify any specific victims, but it hinted at alarm over the findings and a need for organizations to step up their digital defenses, especially when handling massive quantities of sensitive user data. “The advisory details the targeting and compromise of major telecommunications companies and network service providers,” CISA wrote. “Over the last few years, a series of high-severity vulnerabilities for network devices provided cyber actors with the ability to regularly exploit and gain access to vulnerable infrastructure devices. In addition, these devices are often overlooked.”
Separately, hackers likely conducting Chinese espionage breached News Corp in an intrusion that was discovered by the company on January 20. Attackers accessed journalists’ emails and other documents as part of the breach. News Corp owns a number of high-profile news outlets, including The Wall Street Journal and its parent, Dow Jones, the New York Post, and several publications in Australia.
Honorable Mention: California Concealed-Carry Permits
Just days after a consequential US Supreme Court decision at the end of June pertaining to concealed-carry permit laws, an unrelated data breach potentially exposed the information of everyone who applied for a concealed-carry permit in California between 2011 and 2021. The incident impacted data including names, ages, addresses, and license types. The breach occurred after a misconfiguration in the California Department of Justice 2022 Firearms Dashboard Portal exposed data that should not have been publicly accessible. “This unauthorized release of personal information is unacceptable and falls far short of my expectations for this department,” state attorney general Rob Bonta said in a statement. “The California Department of Justice is entrusted to protect Californians and their data. We acknowledge the stress this may cause those individuals whose information was exposed. I am deeply disturbed and angered.”
SOURCE: https://www.wired.com/story/worst-hacks-breaches-2022/
Cryptocurrency is an enabler of cybercrime, says Sygnia exec Guy Segal

Cryptocurrency is the facilitator and enabler of most ransom attacks, according to Guy Segal, vice president cyber security services Asia-Pacific at Sygnia.
Segal describes the relationship between cryptocurrency and cybercrime as multi-dimensional.
“First, whenever you deal with ransom, ransom is being paid in cryptocurrency. Usually, but not always Bitcoin,” he said.
“The other issue is that the cryptocurrency companies – exchange firms – are very fragile and very vulnerable to be under attack. While if you’re attacking a real bank you can damage the bank and you can ask for a ransom, if you’re attacking a cryptocurrency exchange, you can run with the money out of the bank.”
As Bitcoin and the cryptocurrency markets have plummeted in the last few weeks, Segal said that this has had a unique effect on negotiations between victims of cybercrime and the attackers.
“The Bitcoin rate has crashed, I think more than three times lower than the records at the moment, and it’s very dynamic daily. From many threat actors’ point of view, that means that you cannot agree on a deal based on the number of Bitcoins, but the negotiation will be concluded on the US dollar amount.
“For instance, if you could once agree on 40 Bitcoin and then know that it’s going to be around $2 million, now the threat actor doesn’t have any certainty when he agrees on 40 Bitcoins Monday, how much will that be in US dollars, by the end of the week?”
According to Segal, Bitcoin has anonymised threat actors, keeping them safe, secure and largely preventing them from being caught.
New research from cybersecurity company Proofpoint reveals the methods and techniques that threat actors are leveraging to exploit cryptocurrencies and digital tokens or NFTs.
The authors name cryptocurrency credential harvesting, cryptocurrency transfer solicitation and commodity stealers that target cryptocurrency values as the three fundamentals of a phishing campaign targeting crypto.
“Proofpoint researchers observe multiple objectives demonstrated by cybercriminal threat actors relating to digital tokens and finance such as traditional fraud leveraging business email compromise (BEC) to target individuals, and activity targeting decentralised finance (DeFi) organisations that facilitate cryptocurrency storage and transactions for possible follow-on activity. Both of these threat types contributed to a reported $14 billion in cryptocurrency losses in 2021,” the report says.
According to senior director of threat research and detection at Proofpoint Sherrod DeGrippo, “Cybercriminal threats to cryptocurrency are not new, however as the general public experiences growing adoption of cryptocurrency, people may be more likely to engage with social engineering lures using such themes.
“There is no easier method of financial extraction than the illicit transfer of cryptocurrency.”
Hangouts Will Shut Down This Fall as Google Moves People to Chat
For most, conversations will automatically be migrated over from Hangouts to Chat.

Google Hangouts is officially shutting down in November. The search giant is prompting people still using Hangouts to migrate over to Chat as part of its plan to retire the aging messaging platform, the company said in a blog post Monday. Google already transitioned enterprise users earlier this year.
On the Hangouts mobile app, people are being asked to switch to Chat. For those using Hangouts on Gmail through a web browser, Google said it will upgrade people to Chat next month. For most, conversations will automatically be migrated over from Hangouts to Chat, Google said.
Google is also encouraging users to use Google Takeout, the company’s data exportation tool, to download their data before Hangouts ceases operation this November.
Google Hangouts, which launched in 2013, was the company’s chat platform inside Google Plus, a now-defunct social network. Google then added chat functionality to other products, such as Gmail. In 2017, Google launched Chat, a messaging tool for enterprise customers. Chat brought with it new features such as group conversations, side-by-side editing in Docs, Slides and Sheets, and communication within Spaces, the company’s collaboration tool.
Google is moving people from Hangouts to Chat for reasons that include security and regulations.
Chat offers stronger phishing protections by detecting malicious links using real-time data, the company said in a 2020 blog post. US and EU regulations would also make VoIP services subject to the same laws. It’s why Google removed the call phone feature from Hangouts and issued refunds for remaining call credits. Plus, having engineers work on one chat app as opposed to two could be a better allocation of resources.
Internet Explorer is officially dead after 26 years
It’s been the default browsing experience on Windows for 26 years. But now, Internet Explorer is officially dead. Starting on June 15, 2022, the classic Microsoft browser is no longer supported.
The company announced its retirement back in 2021. However, Microsoft is now pushing users to move to Microsoft Edge, its newer, faster, Chromium-based browser.
Internet Explorer is dead, long live Microsoft Edge

If you’ve been using Windows PCs for the last ten years, then chances are you’ve come across Internet Explorer in some form or fashion. While the default Windows browser has evolved some over the years, it’s mostly stayed the same. Now, though, Internet Explorer looks to be officially dead.
Complaints about Internet Explorer have been common for decades, especially since other browsers like Chrome and Firefox began to make a name for themselves. However, in 2017, Microsoft released the first iteration of its new browser, Microsoft Edge, beginning the final demise of the company’s long-standing browser, Internet Explorer.
Microsoft built Edge to replace Internet Explorer and adapt to the needs of modern internet users. Other browsers like Chrome had hit the scene and offered tons of add-ons and features that Internet Explorer just couldn’t keep up with. But the first instance of Edge wasn’t good enough to kill off Internet Explorer.
Sharpening the edge
That, of course, all changed in 2020, when Microsoft released the latest version of Microsoft Edge. Microsoft built this new version off of Chromium, the code behind Google Chrome. And, as such, it offered access to many of the add-ons and features that people had come to love over the years. With Edge offering better options, it seemed that Internet Explorer’s death wasn’t far off.
And now, roughly two years later, Microsoft is finally ready for Internet Explorer to be dead and gone. The company has finally begun the process of pushing Internet Explorer users to Microsoft Edge. Now, when users open Internet Explorer, Microsoft will prompt them to download Edge instead. Starting today, Microsoft considers the browser officially retired.
Not just that. While support for Internet Explorer officially ended today, the program won’t be active for much longer either. In fact, Microsoft says it plans to completely phase it out sometime in the future. Many pages already don’t offer support for the aging browser, and this just seems like a final nail in the coffin.
If you’re still using Internet Explorer for some reason, then it’s probably time to upgrade to Microsoft Edge or one of the other multitude of third-party browsers. Goodness knows there are plenty of great options available these days. If for some reason you need Internet Explorer to access a website, you can make use of Edge’s IE Mode to do so.
Why Clearing the Cache and Cookies on Your Android Phone Is a Good Idea
Does your phone use Google Chrome, Firefox or Samsung Internet? If so, we’ll show you how to boost your privacy (and maybe even speed, too).

Clearing your Android phone browser’s cookies and cache may sound complicated, but it’s actually easier than you might think. It’s a good idea to get into the habit of occasionally clearing out that data no matter which Android smartphone you use. (Yes, that includes the Samsung Galaxy S22 and Google Pixel 6.) Whether your phone uses Google Chrome, Firefox or Samsung Internet, your browser collects and stores data every time you surf the web. This information makes up your cookies and cache, and it helps your phone speedily log in to your accounts and load frequently visited sites.
But this data eventually builds up, taking up space on your phone while also probably including cookies that are tracking your browsing history with the intention of serving personalized advertising. (I’ve been seeing ads for eyeglasses after visiting a few online stores to compare prices and styles, as well as for TV shows related to my YouTube searches.)
It doesn’t hurt to occasionally clear this data out in order to keep your web browser lean, running efficiently and, ideally, storing as few tracking cookies as possible.
On Android, the steps differ slightly depending on the type of phone and web browser app you’re using, so below we’ll go over how to clear this data for Google Chrome browser (often the default for many Android phones like the Google Pixel line), Samsung’s Internet browser (often the default on the Galaxy phone series) and Mozilla’s Firefox browser. You can also check out our separate guide on how to clear your cache on an iPhone web browser in case you have a few Apple devices to clear out, too.
Google Chrome
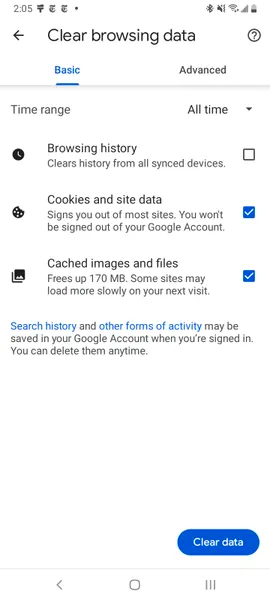
You can delete your cookies and cache from within the Android version of Google Chrome by first tapping the More button in the top right corner of the browser, indicated by a column of three dots, then tapping History, then Clear browsing data. You can also access this from the Chrome Settings menu, tapping Privacy and Security and then Clear browsing data.
Chrome also offers Basic and Advanced settings for clearing your Browsing history, Cookies and site data and Cached images and files. You can use the Time range drop-down to select whether you want to delete the entire history or a selection of anywhere from the past 24 hours up to the last four weeks. Tapping Advanced will also give you access to deleting Saved passwords, Autofill form data and Site settings. After selecting what you want to delete, tap the blue Clear data button, and it will then delete without any other prompts, so just make sure you’re zapping exactly what you want to zap.
Samsung Internet
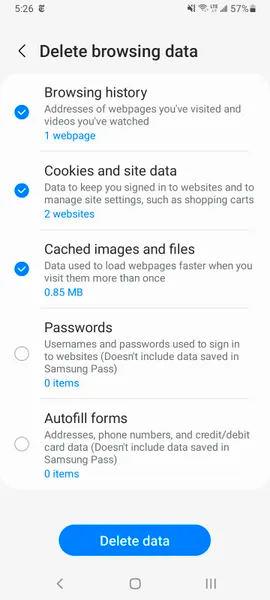
There are two different ways you can clear your Samsung Internet browser’s cache and cookie data. You can clear from within the browser itself, or you can go through your phone’s Settings app.
To clear while in the Samsung Internet browser app, first tap the Options button in the bottom right corner represented by three horizontal lines, then Settings; scroll down to and tap Personal Data, then tap Delete browsing data to get a menu of options to delete. You can clear your Browsing history, Cookies and site data, Cached images and files, Passwords and Autofill forms in any combination. After tapping Delete data, you’ll then receive a prompt asking for you to confirm your choices before deleting.
Going through the browser app itself provides the most customization of what you want to delete. However, if you want to access similar options from your phone’s settings menu, open the Settings app and tap on Apps, then scroll down to and tap Samsung Internet and then Storage.
At the bottom of Storage, you get separate options to Clear cache and Clear data. Tapping Clear cache will immediately delete the cache, but Clear data brings up a prompt that warns you that all of the application’s data will be deleted permanently, including files, settings, accounts and databases. While it doesn’t specify cookies, this “going nuclear” approach should zap all remaining data, letting you restart the Samsung Internet browser as if it were brand-new.
Mozilla Firefox
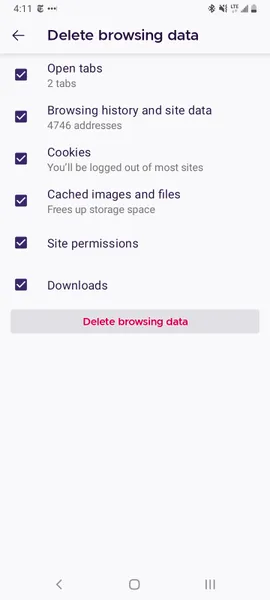
Much as with Google Chrome, you can clear the cookies and cache from within the Mozilla Firefox Android app. To access this function, tap the More button on the right of the address bar, again symbolized by three vertically aligned dots. Then tap Settings and scroll down to Delete browsing data.
Of the three browsers we’re discussing here, Firefox gives you the most options under the Delete browsing data menu, allowing you to also delete any existing Open tabs, your Browsing history and site data, Site permissions and even your Downloads folder alongside Cookies and Cached images and files.
While you can’t pick a time range as you can for Chrome, you can be more specific regarding what type of data you would like to remove.
And Firefox has an additional option for those who never want to keep their browsing data after they’re done using the app. Inside of Settings is a Delete browsing data on quit option, which instructs Firefox to wipe any combination of these same settings every time you quit the application. It’s a useful feature if you’d like to keep the browser tidy and, say, avoid accidentally handing off your browser history to someone who may have stolen or otherwise gained access to your phone.
For more, check out everything to know about Google’s new operating system, Android 13, including how to download the beta now. Also, take a look at CNET’s list of the best Android apps and some settings you’ll want to change on your current phone.
Broadcom to Acquire VMware for $61 Billion
It’s one of the largest tech acquisitions of all time.

Semiconductor company Broadcom is purchasing enterprise software company VMware for $61 billion, the company said in a press release on Thursday. The deal would be one of the largest in tech history.
“This transaction combines our leading semiconductor and infrastructure software businesses with an iconic pioneer and innovator in enterprise software as we reimagine what we can deliver to customers as a leading infrastructure technology company,” said Hock Tran, Broadcom’s president and chief executive officer, in a statement.
The deal has been unanimously approved by the boards of both companies but requires regulatory approval before it can be completed. The deal is expected to close in Broadcom’s fiscal year 2023, which starts in November 2022.
VMware has been part of a larger acquisition before, when Dell bought EMC for $67 billion in 2016. VMWare spun off from Dell last year.
SOURCE: https://www.cnet.com/tech/computing/broadcom-to-acquire-vmware-for-61-billion/
WA gov creates cyber security uplift team
After mandating “essential eight” controls.
The WA government has stood up a strike team to help departments and agencies to uplift their cyber security posture after mandating the Essential Eight cyber security controls last year.
The uplift team, which sits within the Office of Digital Government’s cyber security unit, was made possible with a $25.5 million funding injection in the government’s mid-year budget review.
The funding, provided through the government’s new digital capability fund, will be used to further develop WA’s cyber security capabilities, including incident detection, response and prevention.
It is the first significant investment in cyber security since the Office of Digital Government (DGov) secured $1.8 million in the 2020-21 budget to establish a cyber security operations centre (CSOC).
Speaking to iTnews about the investment, government chief information security officer Peter Bouhlas said the new team had been created to help “agencies to understand where their weak spots are and to provide direct support”.
“It can be overwhelming, with a really long list of things to do, which [controls] to do first,” he said.
“We can help them focus on what’s the one or two or three controls they’re struggling with, and then the team can then go in and have a more targeted approach to supporting an agency.”
Addressing long-held concerns
Initially consisting of five staff, the uplift team will work on a range of different initiatives across a number of agencies, depending on where help is needed.
Around 25 staff will join the cyber security unit in total as a result of the funding, evenly split between policy and operations roles.
DGov has already used surveys to identity weak spots and other areas of concern, though agencies will also be able request help.
“We can see from the survey results and their maturity assessments where they need help,” Bouhlas said.
WA government agencies have struggled with meeting cyber security requirements for many years, as highlighted in numerous information systems reports from the state’s auditor-general.
It’s latest report, published last month, found only 50 percent of agencies met the benchmark for information security in 2021, with “no noticeable improvement from the previous year”.
“Over the last 14 years there has been little improvement in this area with only 11% increase in the number of entities since 2008,” the report said.
From SECC5 to Essential Eight
Bouhlas said much of the focus would be on implementing the Australian Cyber Security Centre’s Essential Eight controls, which has replaced the WA government construct of the SECC5.
SECC5 – or the Security and Emergency Comoittee of Cabinet (SECC) Top Five controls – were initially introduced a “warm up exercise in the lead up to a larger set of controls”.
“Five controls were much easier to talk to and acceptable by agencies to get done, so we focused on that,” he said.
The controls included patching, multi-factor authentication and privileged accounts and backups, but omitted application whitelisting.
“I didn’t think that agencies were ready for that,” Bouhlas said.
As part of the government’s new cyber security policy [pdf], released in October 2021, a new Essential Eight mandate was introduced in part due to the proliferation of cloud services.
The new policy requires agencies to reach a ‘maturity level one’ rating, one level higher than maturity level zero – the lowest level under the Essential Eight maturity model.
The ACSC reintroduced the maturity level zero rating – which signifies weaknesses in an organisation’s overall cyber posture – in a refresh of the controls last year.
“The Essential Eight for us is important because they protect us the majority of attacks that we see across WA, Australia and even globally,” Bouhlas said.
“So, if you’re not doing those and doing them effectively, anything else you are doing could be a waste of time.”
Bouhlas said this decision was made with agencies, who recognised it may result they go “back a level”.
“Unanimously, not one agency said no, we don’t want to do this. They recognised it might be difficult, it might look bad, but that there was a need to improve their cyber security capabilities.”
DGov will report to cabinet on the number of agencies that reach a maturity level one rating under the essential eight and those that don’t.
Greater coordination
The government’s significant investment in DGov’s cyber security unit will also furnish it with a dedicate facility to house the growing team.
“People will have proper facilities to perform the roles that we expect in the modern age,” Bouhlas said.
Funding will also go towards new “tools” like a vulnerability scanner and security information and event management system (SIEM), avoiding the need for agencies to buy their own.
The team will also coordinate with vendors to help industry “understand what DGov is doing” when they engage with agencies.
“Having a central function means we’re sort of orchestrating all of WA’s cyber security industry to get on the same page,” he said.
SOURCE: https://www.itnews.com.au/news/wa-gov-creates-cyber-security-uplift-team-578675
Intel Report Highlights Crucial Role Of Hardware In Future Of Cybersecurity

Cybersecurity has been a persistent and growing challenge since the dawn of the internet. Every advance in technology delivers features and benefits that simplify or automate tasks and streamline productivity, but those benefits also come with consequences. The growth of the technology ecosystem means an expanded attack surface, and threat actors are constantly looking for flaws to exploit or weaknesses in cyber defenses to take advantage of that fact.
Gartner predicted that corporations will spend $172 billion on cybersecurity in 2022. Organizations spend more money every year on cybersecurity tools and initiatives, and yet the volume and impact of cyberattacks increase as well. It seems at face value as if cybersecurity is simply failing, but there are more factors involved—such as the continued growth of connectivity and the exponential increase in the number of devices exposed to risk. There were an estimated 14.6 billion connected devices at the end of 2021 and that number is projected to double by 2027.
The back and forth between cybersecurity solutions and unique attack tools and techniques is somewhat inevitable. There is always a bit of a cat-and-mouse game as cybersecurity vendors evolve new and improved defenses, and threat actors adapt creative new ways to exploit and attack them, but clearly, there is significant room for improvement. Organizations need to take two steps forward to retain an advantage over threat actors, which requires being smarter about cybersecurity—not just spending more money. A new report from Intel examines current trends in cybersecurity spending, and explores what it will take to build a better cybersecurity future and shift things in favor of organizations.
Security Innovation: Secure Systems Start with Foundational Hardware
Intel commissioned the Ponemon Institute to conduct a survey to understand trends in cybersecurity budgets and how organizations are allocating that money to try and stay a step ahead of attackers. Ponemon surveyed 1,406 individuals in the United States, Europe, the Middle East, Africa, and Latin America who influence their organization’s IT decision-making regarding investment in security technologies. The results of the analysis are shared in the report from Intel, “Security Innovation: Secure Systems Start with Foundational Hardware.”
There are a number of valuable insights and takeaways in the report. It offers a glimpse at how organizations are thinking about cybersecurity, and highlights an increased focus on automation and innovations to improve security at the hardware level.
Here are some of the key findings from the report:
- 64% of respondents say their organizations are more likely to purchase technologies and services from technology providers that are leading edge with respect to innovation.
- 36% of respondents have adopted hardware-assisted security solutions and another 47% of respondents say their organizations will adopt these solutions in the next six months (24%) or 12 months (23%).
- Of those same 36% of respondents using hardware-assisted security solutions, 85% say hardware and/or firmware-based security is a high or very high priority in their organization. And 64% say it is important for a vendor to offer both hardware- and software-assisted security capabilities.
“The security threat landscape continues to evolve, becoming more sophisticated and challenging for organizations to defend against,” stated Suzy Greenberg, vice president, Intel Product Assurance and Security, in a press release. “Today more than ever, companies are demanding assurance capabilities and hardware-enhanced security solutions that help protect the entire compute stack. Intel is in a unique position to deliver these innovations on behalf of our customers.”
A More Secure Future
I had the opportunity to attend a virtual panel discussion where Intel’s Suzy Greenberg, and Larry Ponemon from the Ponemon Institute shared their thoughts on the report.
Greenberg noted that the survey and report are not directly related to current events, but pointed out that major issues like the COVID-19 pandemic and the Russian invasion of Ukraine have had a significant impact—accelerating digital transformation, and inflicting chaos in global supply chains. These events also expand the attack surface and create opportunities for threat actors to exploit.
“This past March, the White House requested $32.5 billion in emergency funding and that was to counter COVID-19 and support the war in Ukraine. And you also saw millions of those dollars earmarked to cover a multitude of cybersecurity efforts throughout the federal government and that included securing critical supply chains,” explained Greenberg. “President Biden also recently issued a plea to American businesses really urging them to strengthen their company’s cyber defenses.”
Larry Ponemon summed it up nicely. “Education is so critical because first you have to create awareness, and I think part of the Intel strategy is to do that.”
One of the key areas to raise awareness is the importance of hardware or firmware-based technologies, and the crucial role they can play in preventing exploits and reducing potential risk. For more, you should check out the full report from Intel: Security Innovation: Secure Systems Start with Foundational Hardware.


